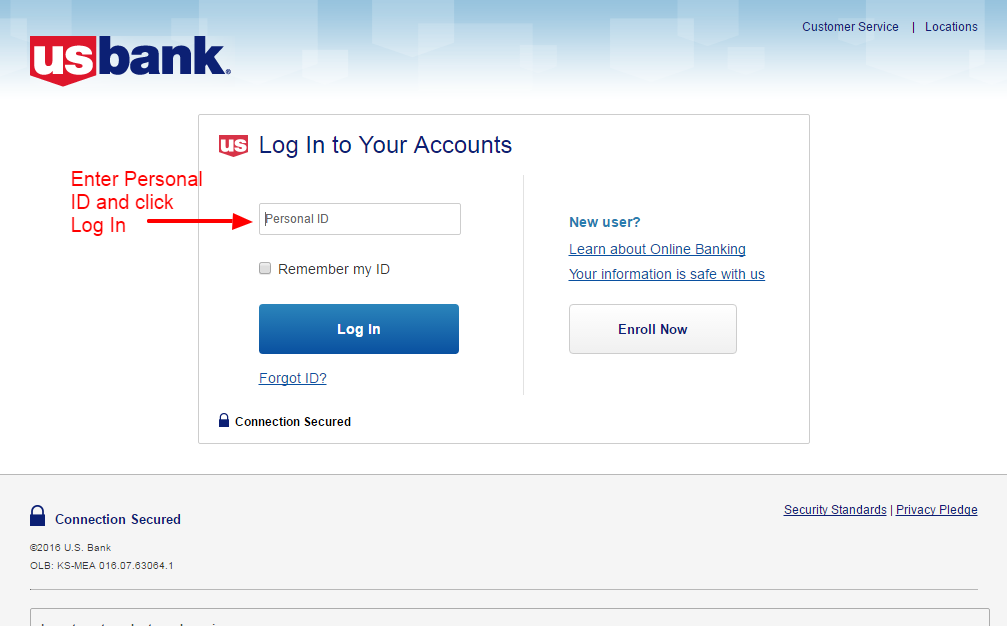
 Card Verification: BIN Checker Software plays a pivotal role in combating payment card cvv2 (https://validsu.su/forgot.Php) (https://validsu.su/forgot.Php) fraud. By validating card details against the issuer’s database, businesses can identify discrepancies and inconsistencies, preventing fraudulent transactions. In conclusion, hackers target bank accounts with credit cards due to the financial gain, potential for identity theft, and demand for stolen data. Recognizing the motives behind these attacks underscores the importance of proactive cybersecurity practices to safeguard sensitive financial information and mitigate the risks associated with cybercrime.
Card Verification: BIN Checker Software plays a pivotal role in combating payment card cvv2 (https://validsu.su/forgot.Php) (https://validsu.su/forgot.Php) fraud. By validating card details against the issuer’s database, businesses can identify discrepancies and inconsistencies, preventing fraudulent transactions. In conclusion, hackers target bank accounts with credit cards due to the financial gain, potential for identity theft, and demand for stolen data. Recognizing the motives behind these attacks underscores the importance of proactive cybersecurity practices to safeguard sensitive financial information and mitigate the risks associated with cybercrime.
Ethical Hacking: Also known as “white hat” hacking, ethical hackers use their skills to identify vulnerabilities in systems, networks, and software. They work to strengthen cybersecurity and protect against potential threats. In conclusion, the world of hacking is a complex landscape with both positive and negative implications. Ethical hacking plays a crucial role in improving cybersecurity and fostering innovation, while malicious hacking poses significant risks to privacy, finances, and digital infrastructure.
As technology continues to evolve, ethical hacking and responsible cybersecurity practices are essential in maintaining a safe and secure digital environment for individuals, businesses, and society as a whole. However, this digital marketplace also presents opportunities for fraudulent actors to create deceptive shopping sites that prey on unsuspecting consumers. This article delves into the world of fraudulent shopping sites, providing insights on how to spot them and offering tips to stay safe while shopping online.
In the age of online shopping, the convenience of making purchases from the comfort of your home is unparalleled. Understanding the signs of fraudulent shopping sites is essential to safeguarding your personal and financial information. Hacking involves exploring and manipulating digital systems to understand their mechanics, improve their functionalities, or unfortunately, exploit their vulnerabilities. In today’s interconnected world, the term “hacking” has become synonymous with both innovation and malicious activities.
This article provides an overview of the world of hacking, its different aspects, and its implications for individuals, organizations, and society as a whole. By recognizing the red flags of fraudulent shopping sites and adopting safe online shopping practices, you can enjoy the benefits of e-commerce while minimizing the risks of falling victim to scams. Remember, staying informed and vigilant is key to navigating the digital marketplace with confidence. The convenience of online shopping shouldn’t come at the cost of your security.